PCNSC Online Practice Questions and Answers
Which PAN-OS policy must you configure to force a user to provide additional credential before he is allowed to access an internal application that contains highly sensitive business data?
A. Authentication policy
B. Decryption policy
C. Security policy
D. Application Override policy
Refer to the exhibit.
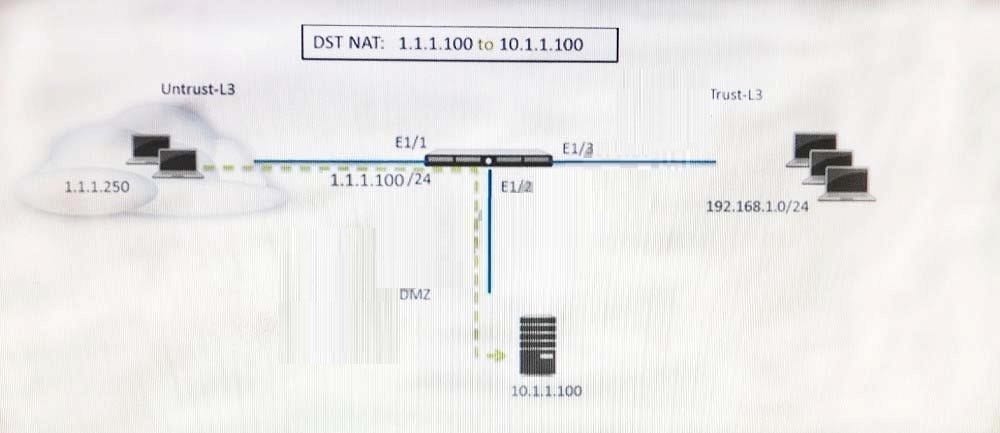
A web server in the DMZ is being mapped to a public address through DNAT. Which Security policy rule will allow traffic to flow to the web server?
A. Untrust (any) to Untrust (10. 1.1. 100), web browsing -Allow
B. Untrust (any) to Untrust (1. 1. 1. 100), web browsing -Allow
C. Untrust (any) to DMZ (1. 1. 1. 100), web browsing -Allow
D. Untrust (any) to DMZ (10. 1. 1. 100), web browsing -Allow
Which User-ID method should b configured to map addresses to usernames for users connected through a terminal server?
A. XFF header
B. Client probing
C. port mapping
D. server monitoring
Which processing order will be enabled when a panorama administrator selects the setting "Objects defined in ancestors will takes higher precedence?
A. Descendant objects, will take precedence over ancestor objects.
B. Ancestor will have precedence over descendant objects.
C. Ancestor objects will have precedence over other ancestor objects.
D. Descendant object will take precedence over other descendant objects.
Which feature prevents the submission of corporate login information into website forms?
A. credential submission prevention
B. file blocking
C. User-ID
D. data filtering
The firewall identified a popular application as a unknown-tcp. Which options are available to identify the application? (Choose two.)
A. Create a Security policy to identify the customer application.
B. Create a customer object for the customer application server to identify the custom application.
C. Submit an App-ID request to Palo Alto Networks.
D. Create a custom application.
Which two methods can be configured to validate the revocation status of a certificate? (Choose two)
A. CRL
B. Cert-Validation-Profile
C. OCSP
D. CRT
E. SSL /TLS Service Profile
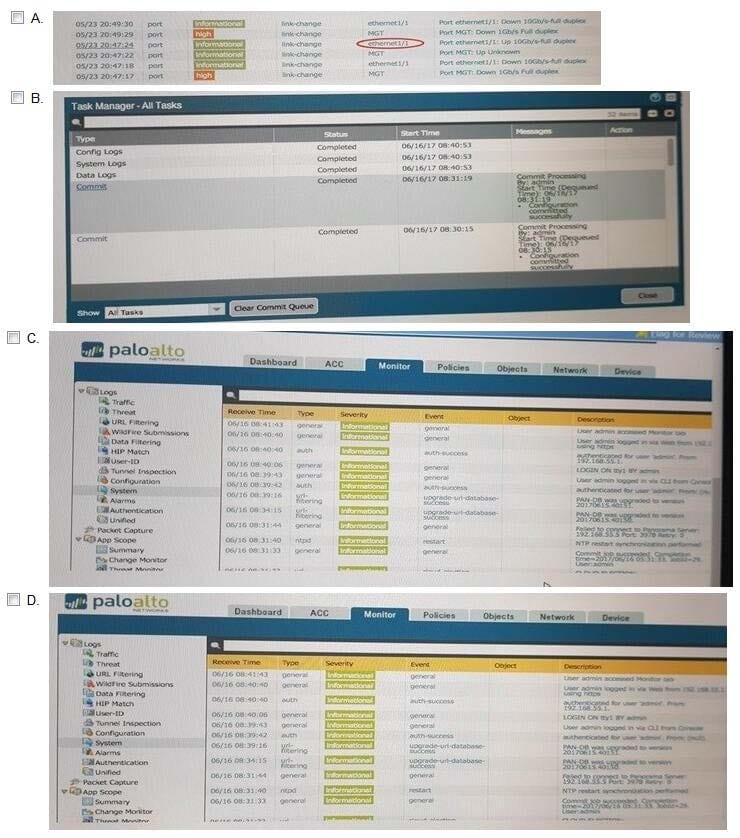
Refer to the exhibit.
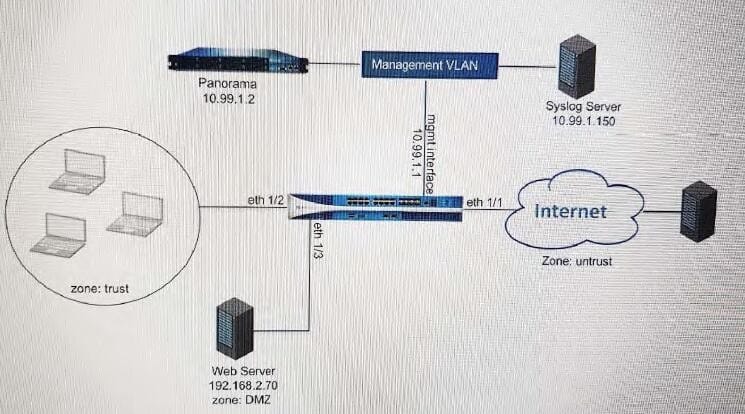
An administrator cannot see any of the Traffic logs from the Palo Alto Networks NGFW on Panorama. The configuration problem seems to be on the firewall side. Where is the best place on the Palo Alto Networks NGFW to check whether the configuration is correct?
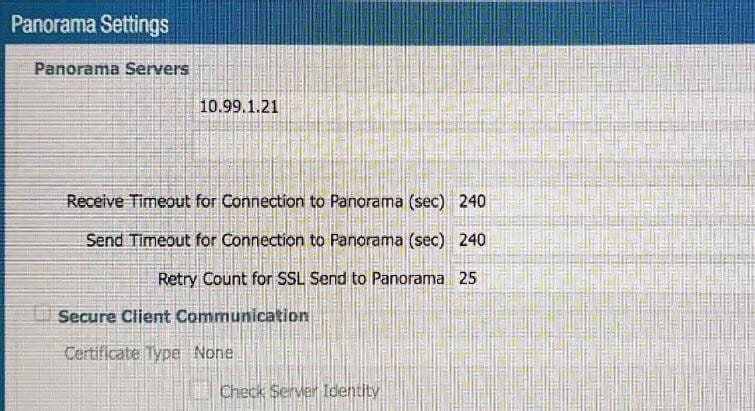
A.
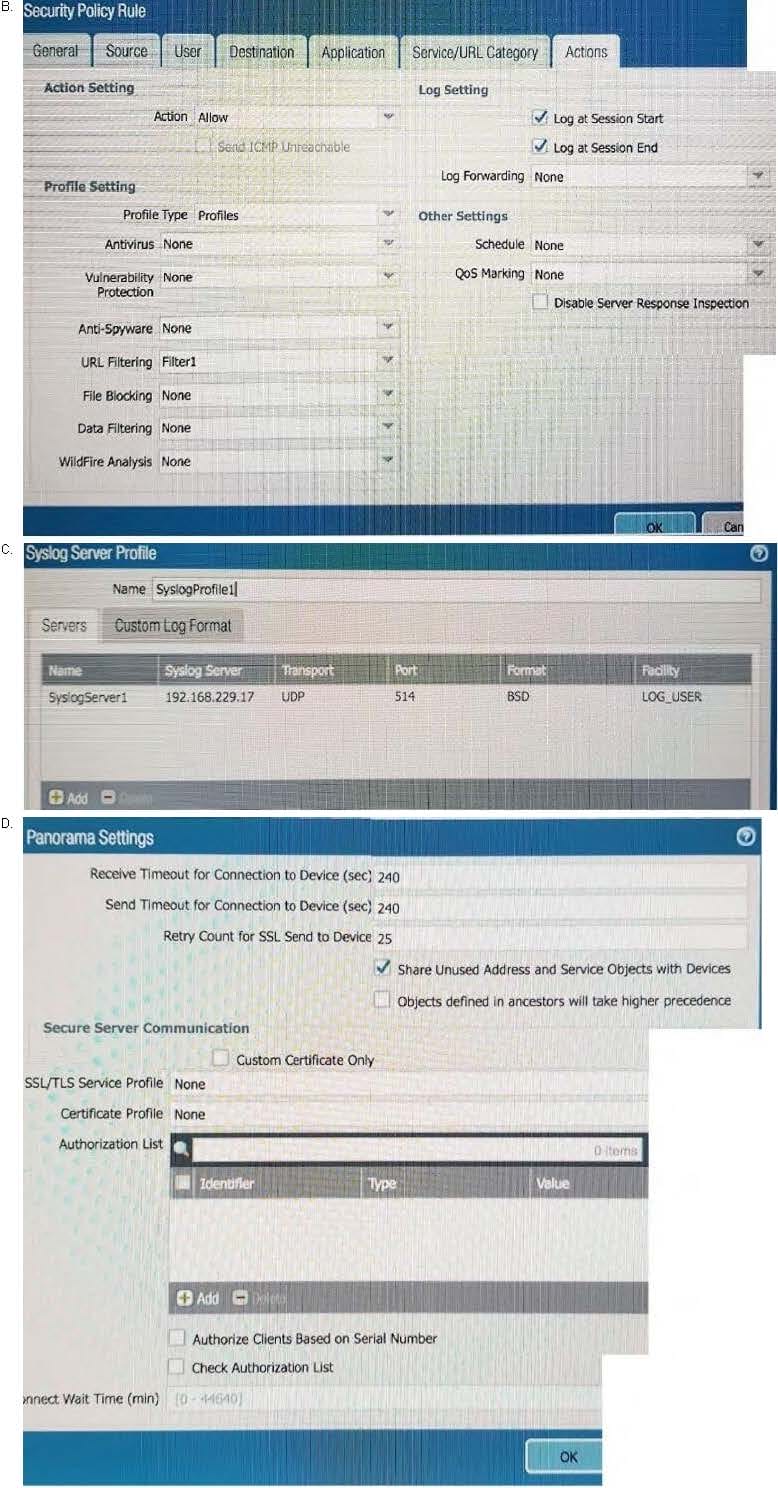
B. C. D.
Winch three steps will reduce the CPU utilization on the management plane? (Choose three. )
A. Disable predefined reports.
B. Reduce the traffic being decrypted by the firewall.
C. Disable SNMP on the management interface.
D. Application override of SSL application.
An administrator accidentally closed the commit window/screen before the commit was finished. Which two options could the administrator use to verify the progress or success of that commit task? (Choose two.)
A. Option A
B. Option B
C. Option C
D. Option D