CISSP-2018 Online Practice Questions and Answers
HOTSPOT
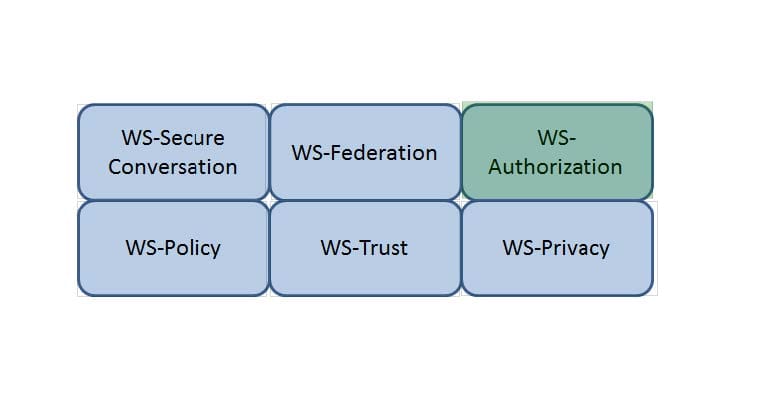
Which Web Services Security (WS-Security) specification handles the management of security tokens and the underlying policies for granting access? Click on the correct specification in the image below.
Hot Area:
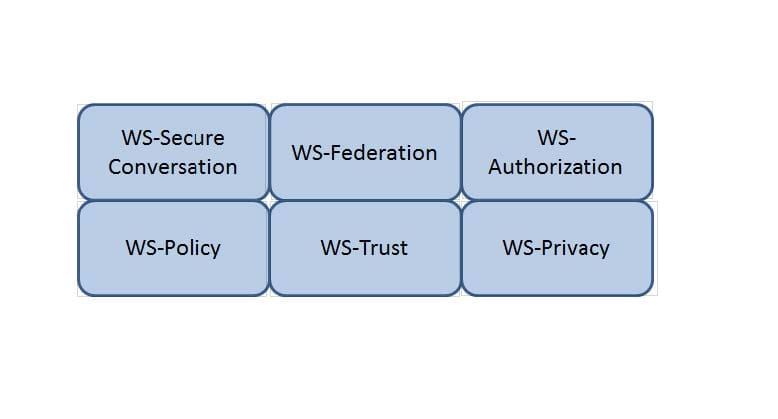
HOTSPOT
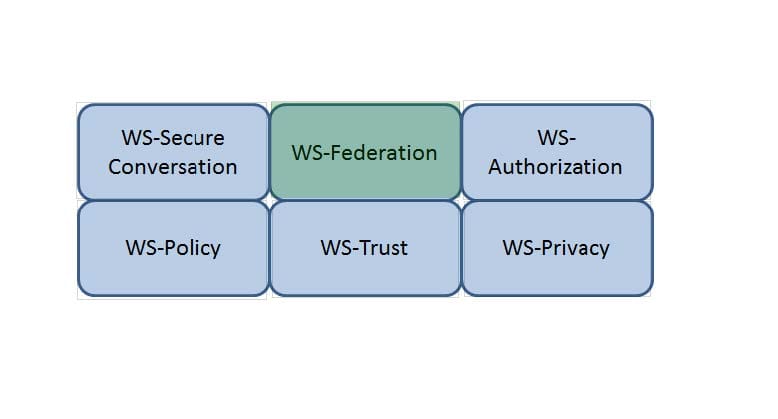
Which Web Services Security (WS-Security) specification maintains a single authenticated identity across multiple dissimilar environments? Click on the correct specification in the image below.
Hot Area:
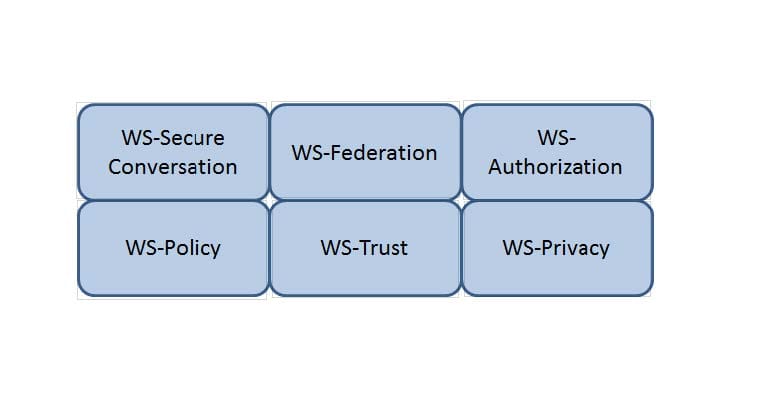
DRAG DROP
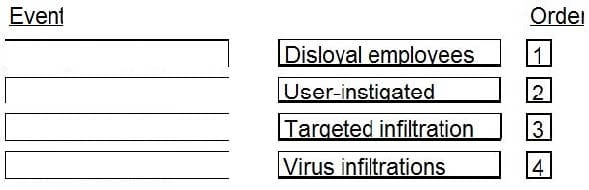
In which order, from MOST to LEAST impacted, does user awareness training reduce the occurrence of the events below?
Select and Place:
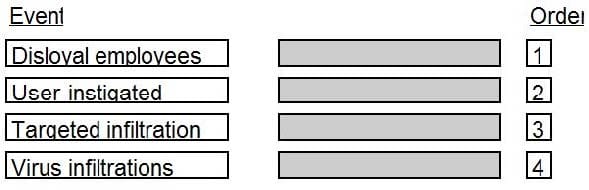
DRAG DROP
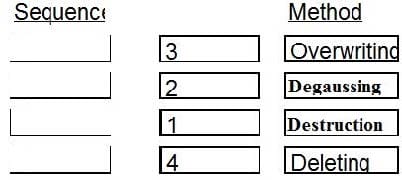
Place in order, from BEST (1) to WORST (4), the following methods to reduce the risk of data remanence on magnetic media.
Select and Place:
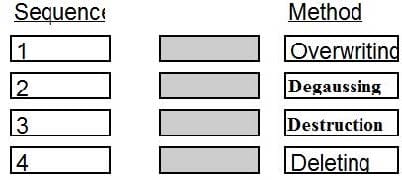
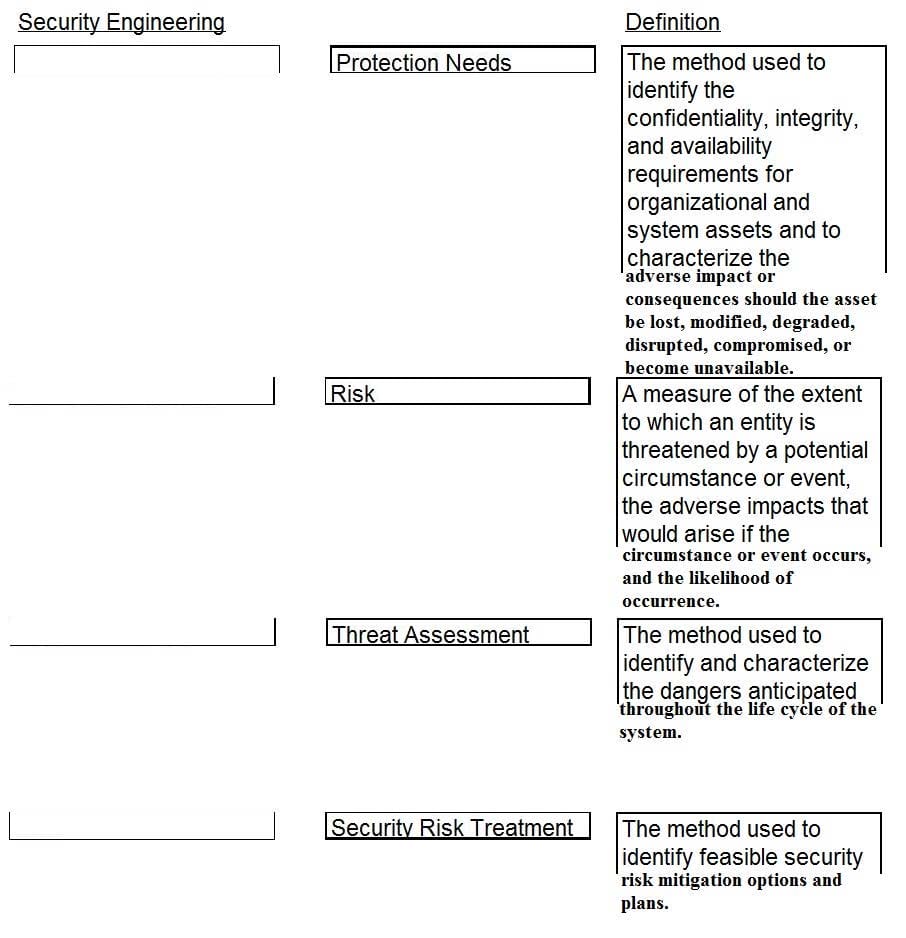
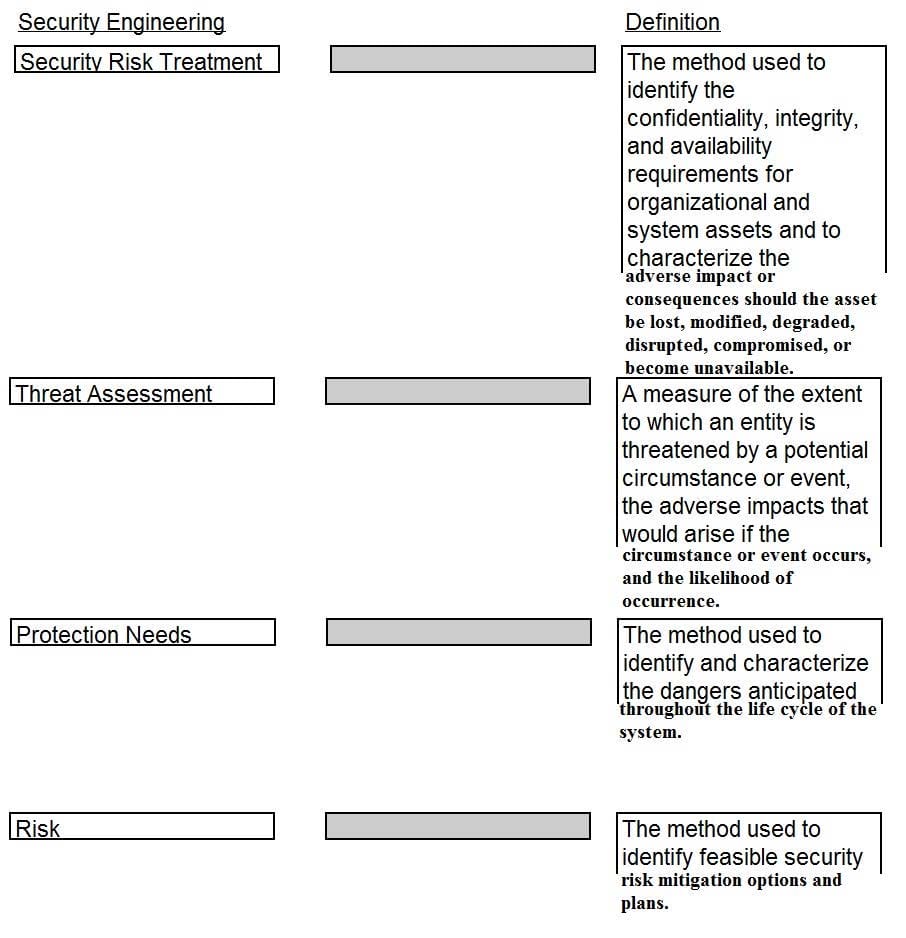
DRAG DROP
Drag the following Security Engineering terms on the left to the BEST definition on the right.
Select and Place:
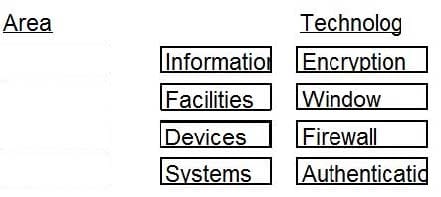
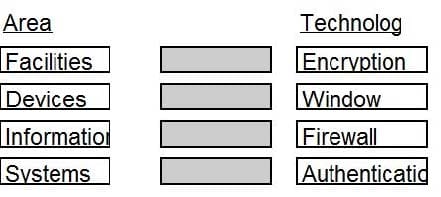
DRAG DROP
Given the various means to protect physical and logical assets, match the access management area to the technology.
Select and Place:
DRAG DROP
Match the objectives to the assessment questions in the governance domain of Software Assurance Maturity Model (SAMM).
Select and Place:

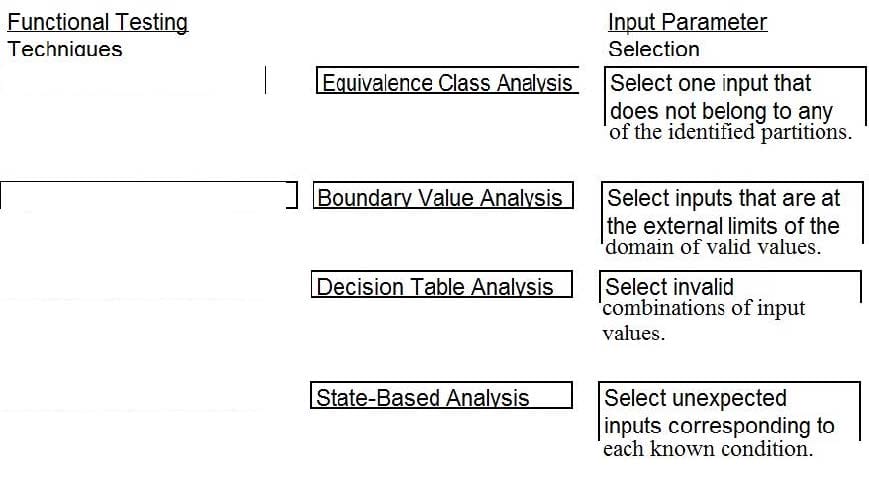
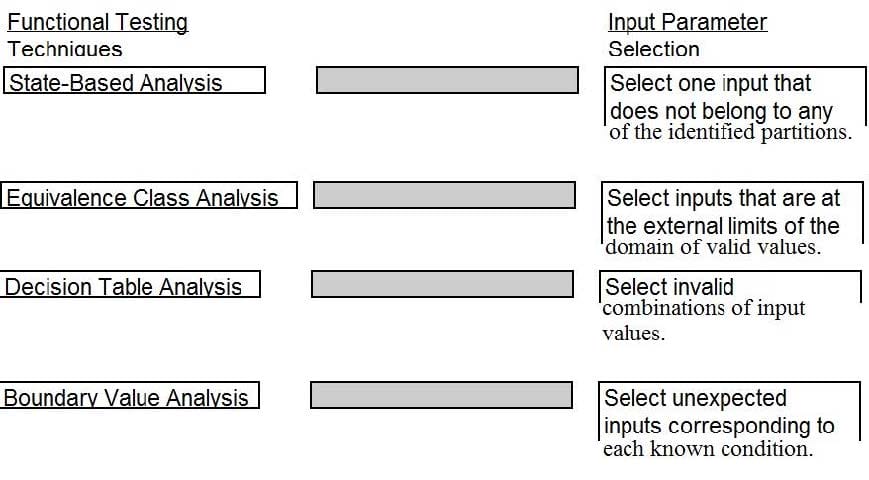
DRAG DROP
A software security engineer is developing a black box-based test plan that will measure the system's reaction to incorrect or illegal inputs or unexpected operational errors and situations. Match the functional testing techniques on the left with the correct input parameters on the right.
Select and Place:
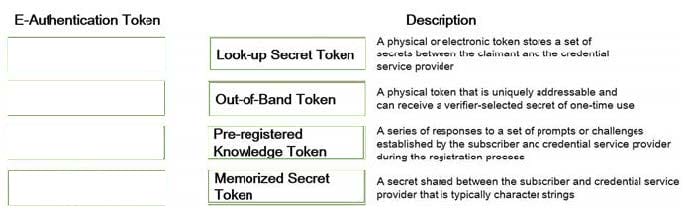
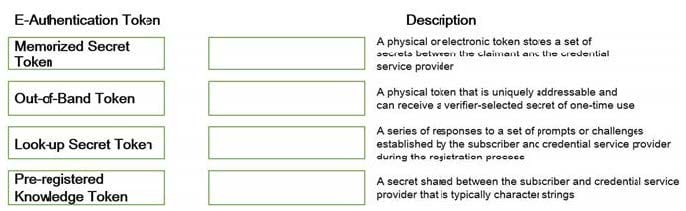
DRAG DROP
Match the types of e-authentication tokens to their description.
Drag each e-authentication token on the left to its corresponding description on the right.
Select and Place:
DRAG DROP
Match the functional roles in an external audit to their responsibilities. Drag each role on the left to its corresponding responsibility on the right.
Select and Place: